Maximise your Network Security resilience.
Mameloo IT provides Network Penetration Services (Pen Testing) to Local Organisations that wish to maximise their Network Security Resilience and eliminate the threat of unauthorised access to their Company and Client data.
Our highly experienced team has conducted Network Penetration Testing services on Computer Networks of all types and sizes. With several years’ collective experience, we have the in-house skills that are needed to optimise your Network Security if you don’t employ an IT expert in-house.
What is Pen Testing and how does it work?
Also known as ‘Pen Testing’ or ‘Ethical Hacking’, Network Penetration Testing is the process of simulating one or more Cyber Attacks on your Network in order to evaluate the effectiveness of your Network Security.
Our Network Penetration specialists will identify and eliminate ANY security vulnerabilities by conducting a series of Cyber Attacks both inside and outside of your Network. We offer solitary Pen Testing Services, or scheduled Penetration Testing to Organisations that require annual tests to maintain their regulatory compliance.
Post Testing Report.
Once the tests are Completed, you will be presented with a full ‘post testing report’ that includes a detailed breakdown of any identified Security vulnerabilities that have the potential to be exploited, together with a list of recommended actions for optimising your Network Security.
Solution Implementation.
If you don’t employ the services of an in-house IT Expert, then our highly skilled Professional IT Consultants will be happy to optimise your Network Security by applying the recommended changes highlighted in your post-testing report.
This service can be conducted outside of standard business hours if we need to conduct any work that could potentially disrupt your daily operations.
WORKING WITH AN ESTABLISHED
Cybersecurity Framework
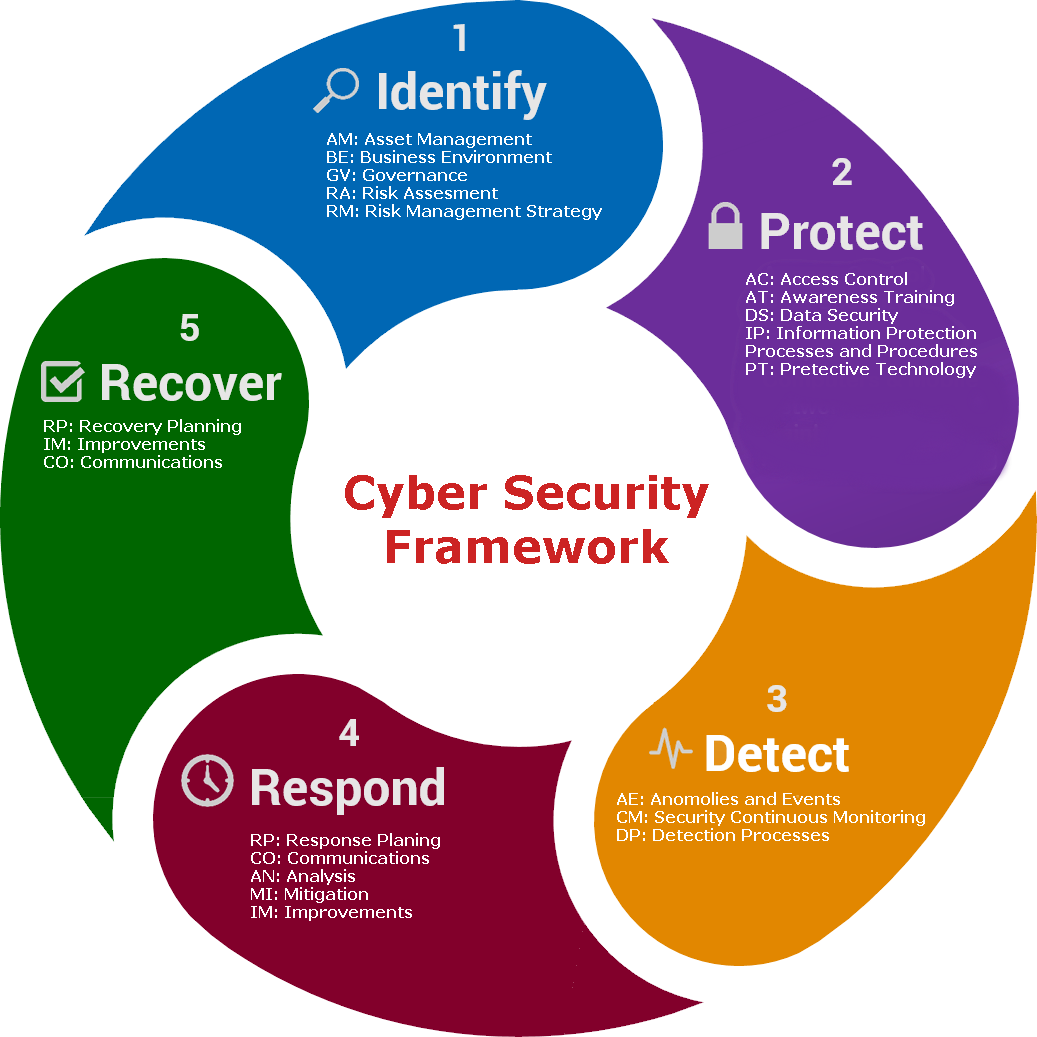
1 – Identify – The ‘identify’ phase covers the information security governance, business processes, asset management, risk management and allows the company to assess its cyber risk prior to an attack in order to allow planning for all phases to take place. This phase should always be revisited after an attack has occurred as it serves to prevent another attack of the same kind.
2 – Protect – The ‘protect’ phase is designed to actively prevent an attack from being successful. This stage consists of a GDPR “Technical Measures” requirement and may also contain “Organisational Measures” designed to prevent a successful attack. The measures are a direct result of your information risk assessment created under the “Identify” phase.
3 – Detect – The ‘detect’ phase provides methods to detect a successful attack. A company cannot assume an attacker will always be thwarted and the “Detect” phase ensures that should any of the protective measures fail – the company can detect and respond (Phase 4) to a breach at the earliest opportunity.
4 – Respond – The ‘respond’ phase details the company’s response to a successful attack – one which may have been detected by the measures in the “Detect phase” or by other means – such as a third party informing the company. The respond phase is considered critical in organisational cybersecurity planning as it defines the actions needed to stop the attack and move into the recovery phase.
5 – Recover – Once the cyber-attack has been stopped and prevented from causing further damage, recovery work must be undertaken to restore services to business as usual. The recovery phase will also include feedback into the “identify” phase to assess how to prevent a similar attack from being successful in future.
Other features of our managed IT support service
Unlimited helpdesk
Email management
Proactive site visits
Network management
Device management
Server management
Managed backup
Strategy planning
