Here’s a breakdown of our Cyber Security Consultancy services…
Initial Risk Assessment Services.
- Our expert Cyber Security Consultants will provide strategic advice and guidance in order to ensure you understand what approach to risk assessment is needed to achieve your security and compliance business objectives
- We will develop a practical view and understanding of the cyber security risks that are associated with your business objectives
- Our experts will then undertake risk assessments and document the results in order to identify and eliminate Cyber Security risks that are relevant to achieving your business objectives
- The results of your risk assessment will support your effective security and business decision making and risk management moving forward
Cyber Security Architecture Implementation Services.
- Our highly experienced experts will ensure you select the right technologies to mitigate any potential vulnerabilities that have been identified in the system architecture
- We will design and develop a series of architectures to manage any identified Cyber Security risks
- We will provide expert guidance on how to greatly mitigate the likelihood of vulnerabilities and exploitation and stifle the impact of a compromise
- We will also provide expert guidance on the planning, secure development, build, deployment and ongoing management of Cyber Security systems and services
Risk Management Services.
- Our Cyber Security Consultants will provide guidance and make recommendations on how to manage Cyber Security and ensure you make develop strategies for future risk management
- We will apply recognised risk management frameworks and/or methods and show you how to apply these methods in the future
- We will work closely with you to develop and document a series of risk management plans that are applicable to your business and are relevant to achieving your business objectives
- We will also provide ongoing guidance to help you develop an approach to ensuring the successful management of identified risks, which will evolve with the newest threats and your changing technology landscape
Cyber Security Audit and Review services.
- Our Cyber Security professionals will provide expert guidance on how to ensure the continuous improvement of internal or external cyber security standards, policies and procedures
- We will provide ongoing support to ensure you maintain your certification or compliance requirements
- We will review your existing cyber security policies and procedures and then recommend any changes or improvements
- In support of the auditing activities, we will review all of your Cyber Security artefacts including designs, risk analysis and security claims provided by third party business partners and service providers
- We will also conduct a series of checks, reviews and audits, in addition to creating detailed reports to give your clients and shareholders the confidence that internal and external cyber security policies, procedures, and external security requirements are being fully complied with.
WORKING WITH AN ESTABLISHED
Cybersecurity Framework
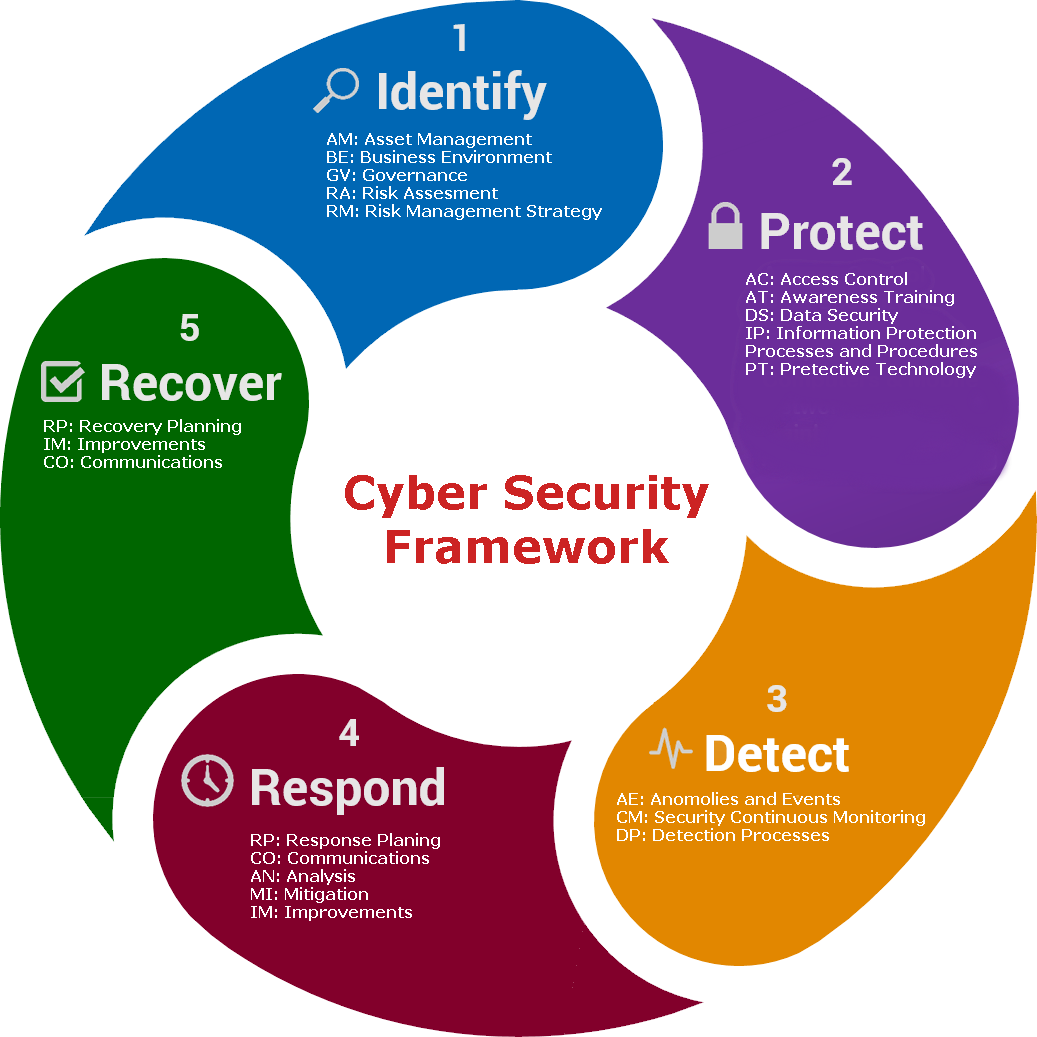
1 – Identify – The ‘identify’ phase covers the information security governance, business processes, asset management, risk management and allows the company to assess its cyber risk prior to an attack in order to allow planning for all phases to take place. This phase should always be revisited after an attack has occurred as it serves to prevent another attack of the same kind.
2 – Protect – The ‘protect’ phase is designed to actively prevent an attack from being successful. This stage consists of a GDPR “Technical Measures” requirement and may also contain “Organisational Measures” designed to prevent a successful attack. The measures are a direct result of your information risk assessment created under the “Identify” phase.
3 – Detect – The ‘detect’ phase provides methods to detect a successful attack. A company cannot assume an attacker will always be thwarted and the “Detect” phase ensures that should any of the protective measures fail – the company can detect and respond (Phase 4) to a breach at the earliest opportunity.
4 – Respond – The ‘respond’ phase details the company’s response to a successful attack – one which may have been detected by the measures in the “Detect phase” or by other means – such as a third party informing the company. The respond phase is considered critical in organisational cybersecurity planning as it defines the actions needed to stop the attack and move into the recovery phase.
5 – Recover – Once the cyber-attack has been stopped and prevented from causing further damage, recovery work must be undertaken to restore services to business as usual. The recovery phase will also include feedback into the “identify” phase to assess how to prevent a similar attack from being successful in future.
Other features of our managed IT support service
Unlimited helpdesk
Email management
Proactive site visits
Network management
Device management
Server management
Managed backup
Strategy planning
