Ransomware Virus
Imagine coming to work, turning on your computer, and being met with a message telling you that your files are now encrypted, and the only way to unlock them is by transferring hundreds if not thousands of dollars to an offshore account. Your IT team isolates the infection and tries to restore from backup only to find that your cloud storage drive has been encrypted as well. All of your business’ data is now being held hostage.
A ransomware virus, a form of increasingly sophisticated malware, has the ability to infiltrate your computer system and encrypt files, in essence locking them up and demanding payment for access. On top of the virus group’s rising complexity, there’s also been a shift in recent years from targeting individuals to targeting businesses and larger institutions. What can your business do to safeguard against such attacks and prevent ransomware before it happens?
Mameloo IT security experts will help you :
Understanding the threat, sophistication, and many faces (and names) of ransomware
How to prevent ransomware attacks by building a multi-layered security infrastructure
The importance and practice of having multiple backups and systems in place to help you protect and manage your important data, as well as training employees on how to spot and mitigate threats
How to take your ransomware prevention and protection program to the next level
WORKING WITH AN ESTABLISHED
Cybersecurity Framework
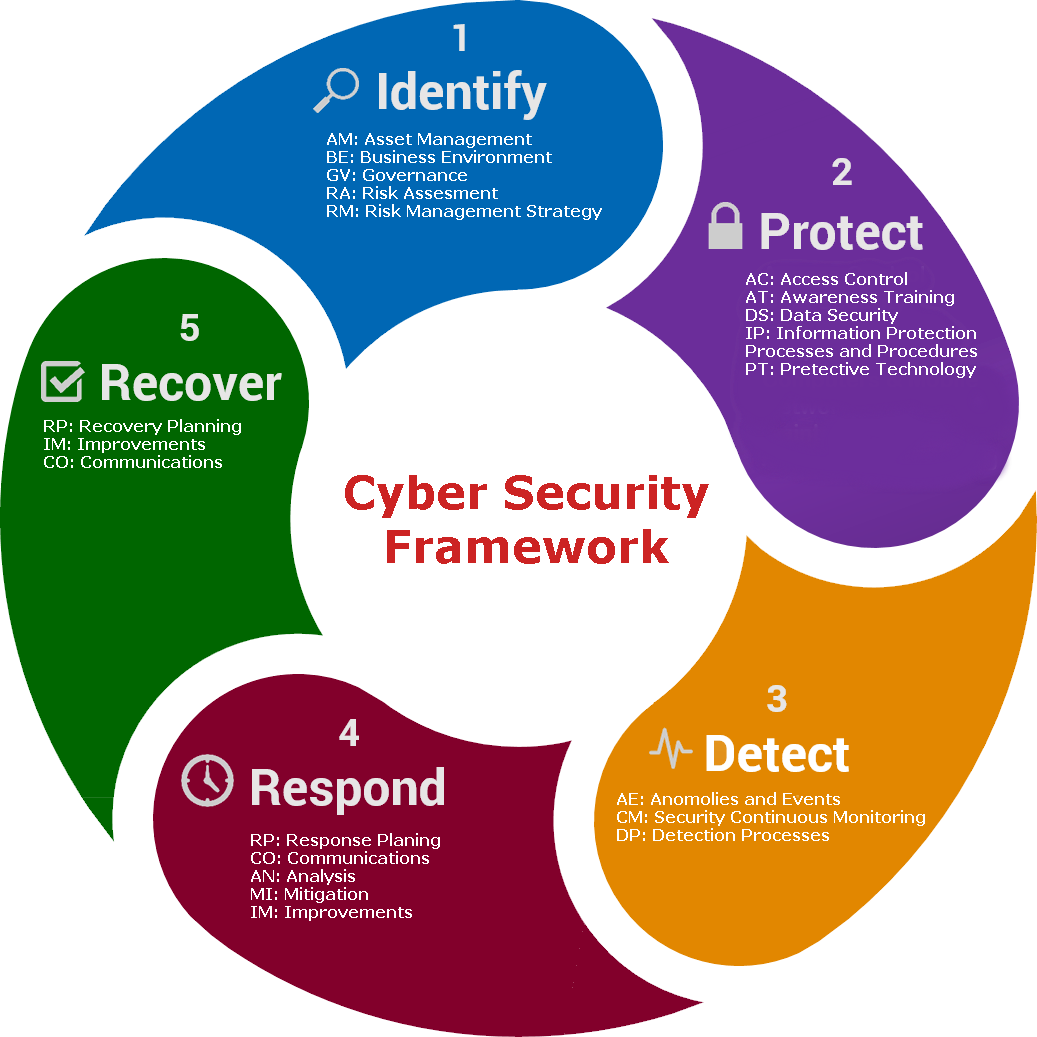
1 – Identify – The ‘identify’ phase covers the information security governance, business processes, asset management, risk management and allows the company to assess its cyber risk prior to an attack in order to allow planning for all phases to take place. This phase should always be revisited after an attack has occurred as it serves to prevent another attack of the same kind.
2 – Protect – The ‘protect’ phase is designed to actively prevent an attack from being successful. This stage consists of a GDPR “Technical Measures” requirement and may also contain “Organisational Measures” designed to prevent a successful attack. The measures are a direct result of your information risk assessment created under the “Identify” phase.
3 – Detect – The ‘detect’ phase provides methods to detect a successful attack. A company cannot assume an attacker will always be thwarted and the “Detect” phase ensures that should any of the protective measures fail – the company can detect and respond (Phase 4) to a breach at the earliest opportunity.
4 – Respond – The ‘respond’ phase details the company’s response to a successful attack – one which may have been detected by the measures in the “Detect phase” or by other means – such as a third party informing the company. The respond phase is considered critical in organisational cybersecurity planning as it defines the actions needed to stop the attack and move into the recovery phase.
5 – Recover – Once the cyber-attack has been stopped and prevented from causing further damage, recovery work must be undertaken to restore services to business as usual. The recovery phase will also include feedback into the “identify” phase to assess how to prevent a similar attack from being successful in future.
Other features of our managed IT support service
Unlimited helpdesk
Email management
Proactive site visits
Network management
Device management
Server management
Managed backup
Strategy planning
