The 25th of May 2018 has come and gone now, but you may find that you are still not compliant with the new General Data Protection Regulation (GDPR).Basically, if you collect, store or handle personally identifiable information of European citizens, you need to ensure that you fully comply with its’ requirements. You have the full responsibility of protecting the data you hold.
Together with our friends at mameloo IT, We will ensure that your business becomes GDPR Compliant by applying appropriate Data Security measures that will protect and secure any personally identifiable data within your Organisation.
The below range of services will enable your business to fully understand exactly what’s needed to comply with the GDPR.
GDPR Gap Analysis.
A GDPR Gap Analysis is applicable to Organisations that wish to identify the remaining steps they need to take in order to become fully GDPR Compliant.
A Data Protection specialist will conduct a rigorous GDPR Gap Analysis, assessing you existing data protection practices and privacy management. They will then provide you with a detailed report that provides a breakdown of your current GDPR Compliance situation, together with a plan of action to address any gaps that will stop you from becoming compliant.
GDPR Data Flow Audit.
A GDPR Data Flow audit is an essential process that will enable your business to implement one or more measures to mitigate the risk of a data security breach. The GDPR Data Flow Audit should be conducted before any subsequent Analysis and training.
After conducting a Data Flow Audit, we will provide your business with a full inventory list of any personally identifiable information that is retained and shared by your Company. This audit will be presented in an easy to understand data flow map.
Data Protection Impact Assessment.
Under the new GDPR regulations, a Data Protection Impact Assessment (DPIA) is a mandatory requirement for when your business applies new Data Processing operations that have the potential to compromise your Clients personally identifiable information, jeopardising their rights and freedoms.
When required, we will conduct an on-site assessment of your new or existing data processing operations. Once this assessment is completed, we will provide you with a report that details any risks associated with these data processing operations, together with a list of recommended controls that should be applied to mitigate risk.
GDPR Training and Awareness.
Our Comprehensive range of GDPR Training and ongoing Awareness courses are designed to ensure that your staff and your managers fully understand their roles and responsibilities under the GDPR. Training courses available include:
- Certified EU General Data Protection Regulation Foundation
- Certified EU General Data Protection Regulation Practitioner
- Data Protection Impact assessment workshop
- GDPR Staff Awareness E-learning course
WORKING WITH AN ESTABLISHED
Cybersecurity Framework
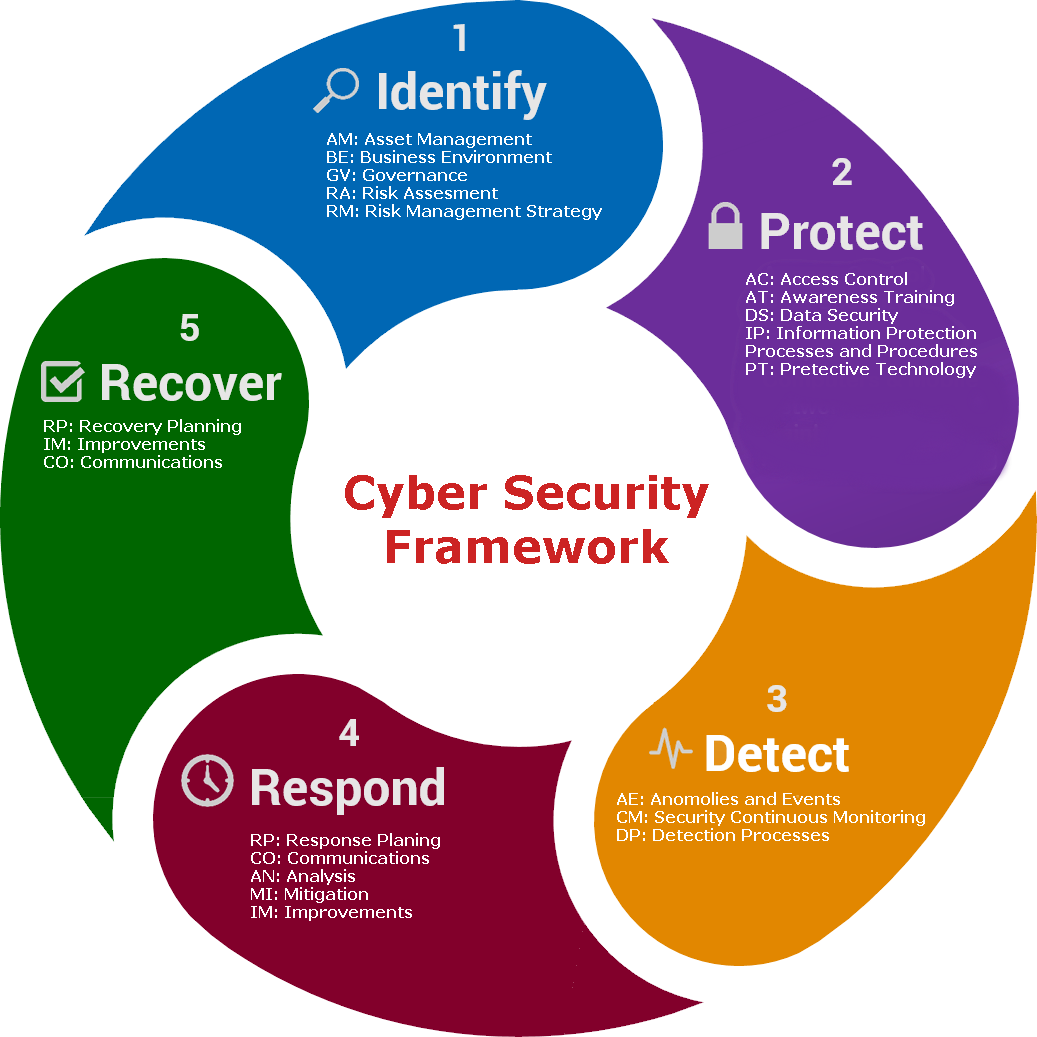
1 – Identify – The ‘identify’ phase covers the information security governance, business processes, asset management, risk management and allows the company to assess its cyber risk prior to an attack in order to allow planning for all phases to take place. This phase should always be revisited after an attack has occurred as it serves to prevent another attack of the same kind.
2 – Protect – The ‘protect’ phase is designed to actively prevent an attack from being successful. This stage consists of a GDPR “Technical Measures” requirement and may also contain “Organisational Measures” designed to prevent a successful attack. The measures are a direct result of your information risk assessment created under the “Identify” phase.
3 – Detect – The ‘detect’ phase provides methods to detect a successful attack. A company cannot assume an attacker will always be thwarted and the “Detect” phase ensures that should any of the protective measures fail – the company can detect and respond (Phase 4) to a breach at the earliest opportunity.
4 – Respond – The ‘respond’ phase details the company’s response to a successful attack – one which may have been detected by the measures in the “Detect phase” or by other means – such as a third party informing the company. The respond phase is considered critical in organisational cybersecurity planning as it defines the actions needed to stop the attack and move into the recovery phase.
5 – Recover – Once the cyber-attack has been stopped and prevented from causing further damage, recovery work must be undertaken to restore services to business as usual. The recovery phase will also include feedback into the “identify” phase to assess how to prevent a similar attack from being successful in future.
Other features of our managed IT support service
Unlimited helpdesk
Email management
Proactive site visits
Network management
Device management
Server management
Managed backup
Strategy planning
